Securing data is the law across several industries and you’re a legal expert. Ensuring your own practice is properly safeguarding client data should be simple, right? Not so much. This means that it’s more important than ever for your firm to rely on IT and cyber security professionals to guide you to cyber safety. There’s a long list of procedures that should be implemented to defend your client data. But without a boots on the ground, first line of defense, they mean nothing. That’s why one of the most important steps is employee security training.
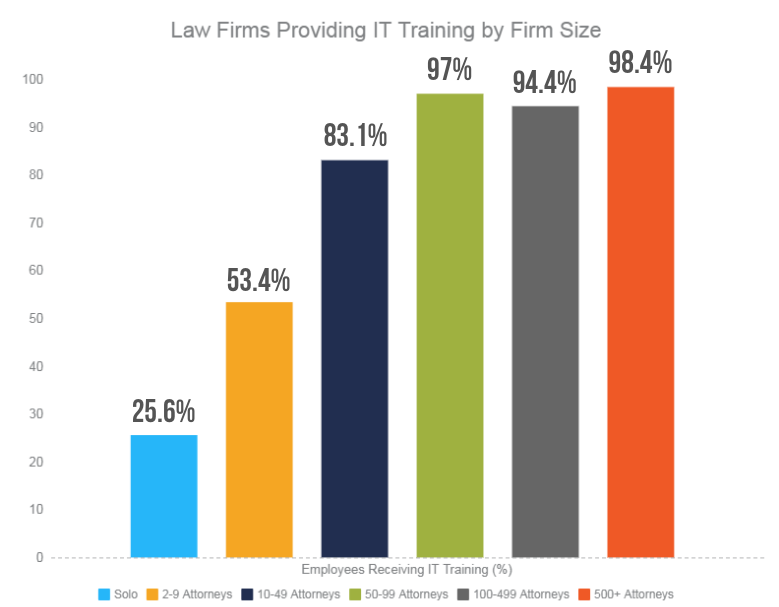
Unfortunately, the ABA Tech Report 2018 found that not all firms are providing technical training. In fact, the number of firms providing training is decreasing. According to the ABA, “Only a slim majority of respondents (56.9%) indicated that there was technology training of any kind available at their firm. This is a marked decline from the 74.3% of respondents who responded affirmatively in 2017, 70.5% in 2016, and 67% in 2015”. Typically, the larger the law firm, the more training is available (below).
Training Topics
While we agree that general technical training is important in today’s email age, firms can’t forget to include cyber security best practices in their training program. Smaller firms, which often invest less in security, are targeted more frequently than those larger firms that train their employees and place an emphasis on technical training.
Here are 5 topics your firm should include in its cyber security curricula:
- PII procedures
- Internal and external security threats
- Phishing awareness
- Password policies
- Physical device protection
PII procedures
Establish and reaffirm proper handling of personally identifiable information (PII). First, make sure your employees know what constitutes as PII. According to Cornell Law School’s Legal Information Institute, “PII means information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other personal or identifying information that is linked or linkable to a specific individual”. Then, think about establishing clean and empty desk policies to limit accidental exposure of PII. Clean and empty desk policy practices include putting away all documents that contain PII at the end of each day and locking your computer whenever you leave your desk.

Internal and external security threats
From ransomware to social engineering or just simple human error, the threat landscape is vast and continues to grow. Your employees should be trained on not only how to detect and prevent threats, but what steps should be taken in the event of a successful attack or data breach. Maintaining up-to-date disaster recovery, incident response, backup, and business continuity plans is critical during any type of security breach. Train your employees to report suspected breaches/infections (like a slow computer, pop-ups, error messages, etc.), any emails sent to the wrong parties, lost or stolen devices/documents, and signs of a physical break-in.

Phishing awareness
One of the most common methods of email malware infection is through phishing attacks [CSO]. Phishing is the malicious attempt to get someone to reveal personal or private information (such as passwords or credit card numbers), often via email. Do your employees know how to spot one? When trying to identify a phishing attempt, your employees should:
- Check for spelling mistakes and broad language (such as “dear customer”)
- Be wary of threats/threatening languages like “you must act now” or “your account will be disabled”
- Question any email that asks for credit card information, passwords, or other confidential information
- Refrain from clicking on suspicious links – hover over links to view the path to make sure it’s what it says it is before clicking
- Avoid downloading unexpected attachments

Password policies
The first line of defense against any good hack is an even better password. According to Microsoft, “banned password lists, multi-factor authentication, detection of password-guessing attacks, and detection of anomalous logon attempts” can also reduce your chances of getting hacked. Need more password ideas? We’ve put this handy guide together to give you some of the pro password tips and tricks that we use to keep accounts secure.

Physical device protection
Any device connected to your network, even personal devices, should have safeguards in place to protect it from physical threats. Your network itself should be segmented so disaster in one area, like a client using your WiFi and accidentally downloading a virus, doesn’t bring down the whole network. Physical device protection also includes employing physical security measures at your building to ensure devices and data don’t get stolen. Employees should know the policies that are in place that address proper trash and electronic device disposal. You can identify any additional physical security needs, such as security cameras or biometric building access, through a comprehensive risk-management process.

You’re Not Alone
If this list of training topics makes you nervous, don’t be. You don’t have to do this all alone. You’re a legal pro, not a tech guru. With a number of training programs, we’re here to help you fill in the gaps. Just click the button below to get started.
You can also click here for a printable infographic to show your team.






