What is NYDFS Cybersecurity Regulation?
The New York Department of Financial Services (NYDFS) Cybersecurity Regulation, or 23 NYCRR 500, is a recently introduced set of cybersecurity regulations directed at financial institutions. Originally announced in 2016 and put into effect on March 1, 2017 – NYDFS regulations featured a phased release to give organizations time to comply. The last of these deadlines occurred in early 2019.
- February 15, 2019: Deadline for certification of compliance by Covered Entities. This is an annual recurrence.
- March 1, 2019: End of two-year transitional period – all Covered Entities must be in compliance with Section 500.11 (Third Party Service Provider Security Policy) of the regulations.
- June 1, 2020: Certification of Compliance due. Due to the COVID-19 outbreak, the deadline for calendar year 2019 has been extended from April 15, 2020 to June 1, 2020.
Who does NYDFS impact?
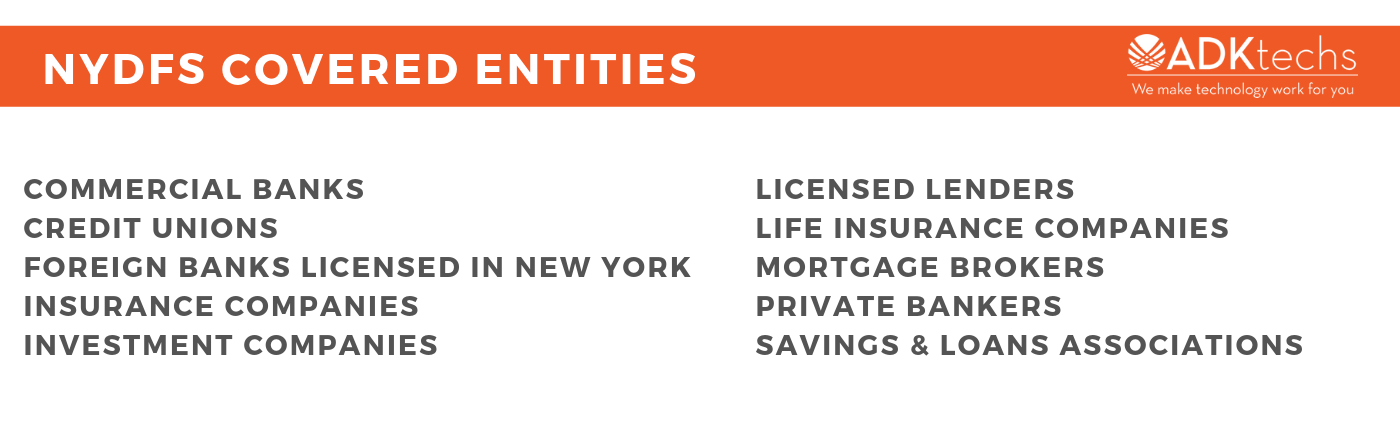
This regulation applies to a number of DFS-regulated organizations such as:
- Commercial banks
- Credit unions
- Foreign banks licensed in New York
- Insurance companies
- Investment companies
- Licensed lenders
- Life insurance companies
- Mortgage brokers
- Private bankers
- Savings & loans associations
These organizations are referred to as Covered Entities. A Covered Entity is “any Person operating under or required to operate under a license, registration, charter, certificate, permit, accreditation or similar authorization under the Banking Law, the Insurance Law or the Financial Services Law”.
However, companies that fall under any of these three categories are exempt:
- Fewer than 10 employees, including any independent contractors, of the Covered Entity or its Affiliates located in New York or responsible for business of the Covered Entity
- Less than $5,000,000 in gross annual revenue in each of the last three fiscal years from New York business operations of the Covered Entity and its Affiliates
- Less than $10,000,000 in year-end total assets, calculated in accordance with generally accepted accounting principles, including assets of all Affiliates
What are the NYDFS requirements?
NYDFS Cybersecurity Regulation requirements aim to protect businesses and consumers through the use of common sense cybersecurity practices. They essentially require regulated institutions to implement, maintain, and annually certify that they have cybersecurity programs in place to protect the integrity of their information systems. Please note that the regulations below have been edited for clarity and succinctness. You can view our easy to digest infographic here or read the full 23 NYCRR 500 document here.
Each Covered Entity must implement a cybersecurity program that:
- Identifies and assesses internal and external threats
- Uses defensive measures to protect information systems and private information
- Detects, responds to, and recovers from cybersecurity events
- Meets applicable regulatory reporting obligations
Each Covered Entity must implement and maintain written policies that address the following areas:
- Information security
- Data governance and classification
- Asset inventory and device management
- Access controls and identity management
- Business continuity and disaster recovery planning and resources
- Systems operations and availability concerns
- Systems and network security
- Systems and network monitoring
- Systems and application development and quality assurance
- Physical security and environmental controls
- Customer data privacy
- Vendor and Third Party Service Provider management
- Risk assessment
- Incident response
A Chief Information Security Officer (CISO) must be designated to enforce each Covered Entity’s cybersecurity program and policies. The CISO can be employed by the Covered Entity, one of its Affiliates, or a Third Party Service Provider.
The cybersecurity program for each Covered Entity should include monitoring and testing, developed in accordance with the Covered Entity’s Risk Assessment, designed to assess the effectiveness of the Covered Entity’s cybersecurity program. This includes:
- Annual penetration testing
- Bi-annual vulnerability assessments
Each Covered Entity must securely maintain systems that, to the extent applicable and based on its Risk Assessment are designed to reconstruct material financial transactions sufficient to support normal operations and obligations of the Covered Entity and include audit trails.
Covered Entities should limit user access privileges to Information Systems that provide access to Nonpublic Information. These access privileges should be periodically reviewed.
Cybersecurity programs must include written procedures, guidelines and standards designed to ensure the safety of internally and externally developed applications. These procedures should be reviewed and updated periodically.
Periodic documented Risk Assessments should be conducted to update and revise existing policies to account for evolving threats.
In addition to the CISO, each Covered Entity will employ qualified cybersescurity personnel (via Covered Entity, an Affiliate or a Third Party Service) to manage cybersecurity risks and oversee the Cybersecurity Program. Covered Entities must:
- Provide cybersecurity personnel with cybersecurity updates and training sufficient to address relevant cybersecurity risks
- Verify that key cybersecurity personnel take steps to maintain current knowledge of changing cybersecurity threats and countermeasures
Covered Entities must implement written policies and procedures designed to ensure the security of Information Systems and Nonpublic Information that are accessible by Third Party Service Providers. These policies must address:
- Identification and risk assessment of Third Party Service Providers
- Minimum cybersecurity practices required to be met by such Third Party Service Providers in order for them to do business with the Covered Entity
- Due diligence processes used to evaluate the adequacy of cybersecurity practices of such Third Party Service Providers
- Periodic assessment Third Party Service Providers based on the risk they present and the continued adequacy of their cybersecurity practices
Based on its Risk Assessment, each Covered Entity will use effective controls, which may include Multi-Factor Authentication or Risk-Based Authentication, to protect against unauthorized access to Nonpublic Information or Information Systems. Multi-Factor Authentication should be used by any individual accessing the Covered Entity’s internal networks from an external network, unless the Covered Entity’s CISO has approved in writing the use of reasonably equivalent or more secure access controls.
As part of its cybersecurity program, each Covered Entity shall include policies and procedures for the secure disposal on a periodic basis of any Nonpublic Information that is no longer necessary for business operations.
Each cybersecurity program should:
- Implement risk-based policies, procedures and controls designed to monitor the activity of Authorized Users and detect unauthorized access or use of, or tampering with, Nonpublic Information by such Authorized Users
- Provide regular cybersecurity awareness training for all personnel
As part of its cybersecurity program, based on its Risk Assessment, each Covered Entity must implement controls, including encryption, to protect Nonpublic Information held or transmitted by the Covered Entity both in transit over external networks and at rest.
Each Covered Entity must establish a written incident response plan designed to promptly respond to, and recover from, any Cybersecurity Event. It should address:
- Internal processes for responding to a Cybersecurity Event
- Goals of the incident response plan
- Definition of clear roles, responsibilities and levels of decision-making authority
- External and internal communications and information sharing
- Identification of requirements for the remediation of any identified weaknesses in Information Systems and associated controls
- Documentation and reporting regarding Cybersecurity Events and related incident response activities
- Evaluation and revision as necessary of the incident response plan following a Cybersecurity Event
Covered Entities must notify the NYDFS superintendent within 72 hours after noticing a Cybersecurity Event that has a reasonable likelihood of materially harming any material part the Covered Entity’s IT infrastructure. An annual compliance statement covering the previous calendar year must be submitted by February 15th. Each Covered Entity should maintain all records, schedules, and data supporting this certificate for a period of five years.
Why should my organization comply?
Financial Implications
Even though NYDFS has been quiet on exact fines, it’s safe to assume that they could get pretty steep. Many experts believe that they will be calculated based upon existing New York Banking Law penalties:
- $2,500 per day during which a violation continues
- $15,000 per day in the event of any reckless or unsound practice or pattern of misconduct
- $75,000 per day in the event of a knowing and willful violation
It’s important to keep in mind that these fines are in addition to any other financial losses your institution would face in the aftermath of a data breach or Cybersecurity Event, loss of customer confidence, and PR hits.
The Impact of COVID-19
Thanks to an uptick in remote workers and increased phishing attempts, COVID-19 has increased NYDFS focus on cyber security even more. Over the last few months, the department has issued a number of letters addressing the rising occurrence of cyber threats due to the pandemic. Included in these letters was the previously mentioned filing extension for 2019 and a directive for all regulated businesses to submit a plan “to address operational risks posed by the outbreak of a novel coronavirus,” including “assessment[s] of potential increased cyber-attacks and fraud.”
FALLING BEHIND?
Get compliant with help from ADKtechs.
From cyber security planning & consulting to risk assessments and penetration testing, we’ll be your guide along the road to compliance.






