Hackers target attorneys. According to the National Law Review, “As more and more clients send cyber due-diligence questionnaires to outside counsel to confirm that their sensitive information is secure, law firms have shored up their defenses, but a recent report by Logicforce found that is just not enough. Of the 200 law firms surveyed for their Q1 2017 Law Firm Cyber Security Scorecard, every one was targeted for confidential client data in 2016–2017, and approximately 40% did not know they had been breached. The report also found that the size of the firm made no difference: Large and small firms alike were targets. Logicforce’s Q4 2017 Law Firm Cyber Security Scorecard didn’t note much improvement by the end of the year. In fact, 48% of law firms had their data security practices audited by at least one corporate client in the past year”.
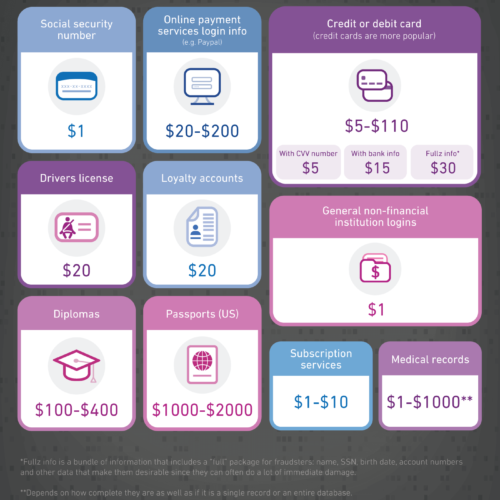
This report further reinforces the fact that any business that handles personal information has a giant target on its back, regardless of size or industry. Cyber criminals can make a pretty penny off of the personal information of each of your clients, such as social security number, driver’s license, or credit card. Supplement any of this sensitive data with information as simple as a name or DOB to create a “fullz” and fraudsters can cause a lot of damage. Experian laid it all out in the infographic below:
As we’ve mentioned before, for those in the legal industry, there’s the additional pressure of guidelines and ethical responsibilities that make safeguarding client data a #1 priority. Here are the top 4 cyber security threats right now for attorneys in the digital world:
Phishing
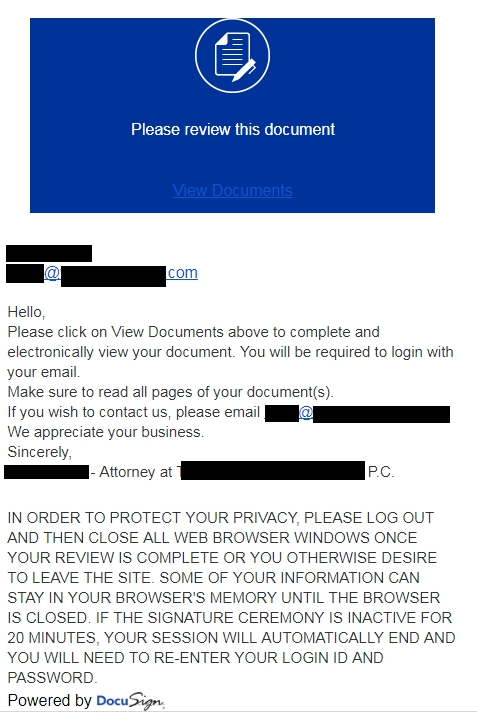
Lawyers are constantly using email and online tools, like DocuSign and Dropobox, to communicate or share files throughout the day. Cyber criminals use this knowledge to exploit unsuspecting victims by sending DocuSign or Dropbox phishing emails, telling a user that it’s urgent for them to click a link, log in, or download a file. Once you click a link, you’re redirected to a phishing site that asks for your credentials. A phishing site is like a phishing email in that it often tries to trick you into giving up personal information by mimicking a trusted source, right on down to the logo and color scheme. These sites look legitimate upon first glance, but are bad news. Sophisticated hackers even use SSL encryption (signified by a lock and https at the beginning of a web address) to make a site appear reputable, as seen below. Always be sure to look at the address closely to confirm if you’re actually where it says you are. Ssymarecords.com ≠ docusign.com. If you enter your password into one of these phishing sites, a cyber trickster could access any client files and information you have tied to that account; and if you use the same password over and over, those accounts are at risk, too.

Recently, the Texas Lawyers’ Insurance Exchange received a DocuSign phishing scam. The email asked that they click a link to log in to their account to view a file. It appeared to come from a law firm and even had the DocuSign logo at the bottom of the email. They called the phone number in the email instead of clicking and were told that they needed to click that link right away to see the file. Any sense of urgency tied to an unexpected email should be a red flag. You’ll also notice in the screenshot of the suspicious email (below), that the note at the bottom of the email doesn’t quite use natural language and is worded weirdly – another red flag.
There are many specific steps lawyers can take to avoid falling for a phishing scam and compromising their client information:
- Establish proper electronic communication procedures with your clients at the beginning of each case.
- Use strong passwords on all accounts. Don’t reuse them.
- Encryption. Encryption. Encryption.
- Use antivirus software, spam protection, and a good firewall.
- Ensure all personnel are trained on cyber security best practices.
- Hover over links in an email to see where it actually leads.
- Never enter a password or other information on a website clicked in an email. Instead, open up your browser of choice and go directly to the site.
- Understand both lawyer and client responsibilities under state and federal law for data protection.
- Use client portals for transmission of client information, if possible.
Malware
“Malware” is the term used to describe any type of malicious software that is intended to damage or disable a computer or computer system. From highly dangerous to simply annoying, it’s something your firm wants to avoid.
In 2017, global law firm DLA Piper was hit with a nasty attack – NotPetya. An attack that cost them 15,000 hours of IT staff overtime and ultimately ended with them wiping their entire system.
NotPetya is similar to the world-renowned Petya ransomware. They’re both pieces of malware that encrypt files and demand a ransom, but that’s where the similarities stop. NotPetya doesn’t require human intervention, like clicking a link, to spread. It also encrypts everything, not just the master boot file. Lastly, despite locking users out of their data and demanding a ransom, it’s not actually ransomware. According to CSO, “It looks like ransomware, complete with a screen informing the victim that they can decrypt their files if they send Bitcoin to a specified wallet. For Petya, this screen includes an identifying [code] that they’re supposed to send along with the ransom; the attackers use this code to figure out which victim just paid up. But on computers infected with NotPetya, this number is just randomly generated and would be of no help in identifying anything. And it turns out that in the process of encrypting the data, NotPetya damages it beyond repair”.
Some safeguards against malware include firewalls, backups, anti-virus software, keeping your OS up to date, and training your employees.
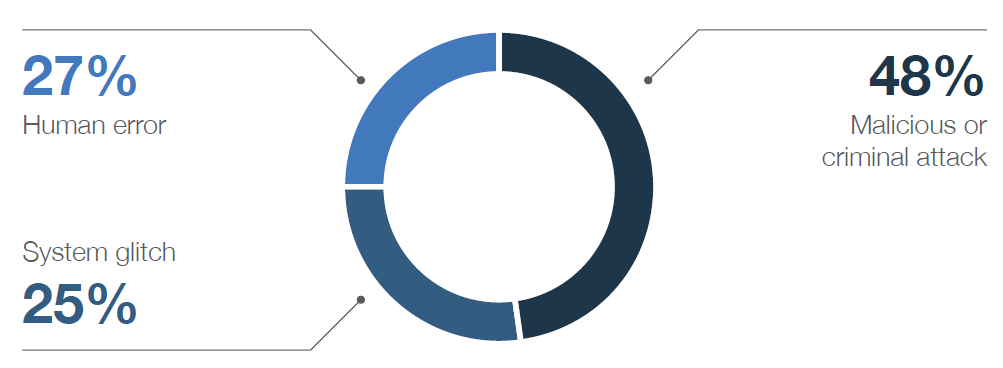
Human Error
Accidents happen and occasionally, they’re catastrophic. In fact, human error is one of the leading causes of data breaches. An overly trusting paralegal clicks a phishing link. A distracted assistant mistakenly sends confidential documents to the wrong person. An at-work selfie with open case files on a lawyer’s desk turns into a data leak ((that laptop glow offers perfect lighting). A mix-up at the airport sends your laptop to the wrong Portland. But if accidents are inevitable, what can a law firm do to combat them? Combining data privacy and cyber security policies & procedures with a response plan is a good start. As technology becomes more ingrained in day to day operations, these policies and procedures need to be frequently assessed and adjusted to ensure continued efficacy.
Malpractice Allegations
In 2018, the American Bar Association released a report detailing attorney obligations when it comes to data security and breach disclosure, “Lawyers must employ reasonable efforts to monitor the technology and office resources connected to the internet, external data sources, and external vendors providing services relating to data and the use of data.” When a data breach involving client information occurs, “lawyers have a duty to notify clients of the breach.” The report also restated that law firms have an inherent ethical responsibility to maintain client privacy when transmitting information over the internet.
Even if a breach hasn’t happened yet, you can still face malpractice allegations for lax cyber security practices.
Now your reputation is damaged. If a breach actually occurred, you may have lost a lot of data. And it turns out, cyber liability insurance only goes so far (or sometimes doesn’t go anywhere at all). The American Bar Association said it best, cyber liability policies “often include requirements for security audits and include language about conforming to industry cyber security standards. The quintessential ‘we don’t cover stupid’ case is Columbia Casualty Co. v. Cottage Health System. There are now more cases where insurers are saying that the insured did not take the reasonable security steps required by the policy”.
Check out our handy infographic here.