For the last 13 years, Verizon has released a comprehensive report on the state of global cyber security incidents and data breaches. The report spans various industries and we encourage you to check it out for yourself by clicking here. In honor of National Cyber Security Awareness Month, we’ve highlighted some statistics that you may find shocking from this year’s 2020 Verizon Data Breach Investigations Report (DBIR) below.
Terms
Before we get started, there are some definitions directly from Verizon that will make all the data below easier to understand:
VERIS resources
The terms “threat actions,” “threat actors” and “varieties” will be referenced a lot. These are part of the Vocabulary for Event Recording and Incident Sharing (VERIS), a framework designed to allow for a consistent, unequivocal collection of security incident details. Here is how they should be interpreted:
Threat actor: Who is behind the event? This could be the external “bad guy” that launches a phishing campaign or an employee who leaves sensitive documents in their seat-back pocket.
Threat action: What tactics (actions) were used to affect an asset? VERIS uses seven primary categories of threat actions: Malware, Hacking, Social, Misuse, Physical, Error and Environmental. Examples at a high level are hacking a server, installing malware and influencing human behavior through a social attack.
Variety: More specific enumerations of higher-level categories, e.g., classifying the external “bad guy” as an organized criminal group or recording a hacking action as SQL injection or brute force.
Incident vs breach
We talk a lot about incidents and breaches and we use the following definitions:
Incident: A security event that compromises the integrity, confidentiality or availability of an information asset.
Breach: An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
Results Overview
For this year’s report, Verizon collected data on 157,525 incidents and 108, 069 data breaches.
Threat Actions
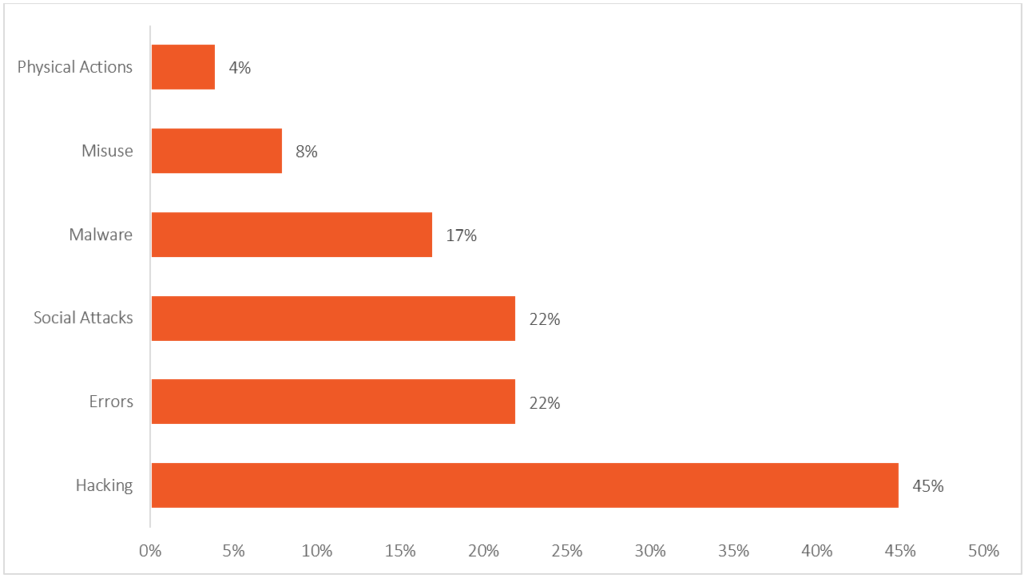
Verizon found that the top 4 tactics that caused a breach were hacking (45%), errors (22%), social attacks (22%), and malware (17%).
Threat Actors
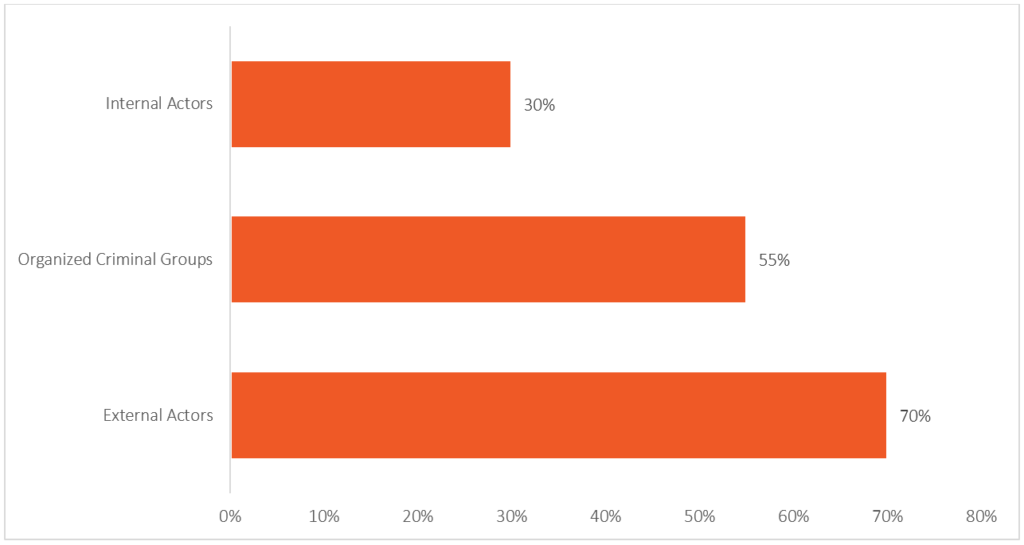
The report shows that most breaches were executed by external actors (70%). Organized criminal groups and internal actors were the next most common breach perpetrators at 55% and 30%, respectively. According to the FBI Internet Crime Complaint Center (IC3), 85% of threat actors were located in the same country as their victims, 56% were located in the same state, and 35% were located in the same city.
Victims
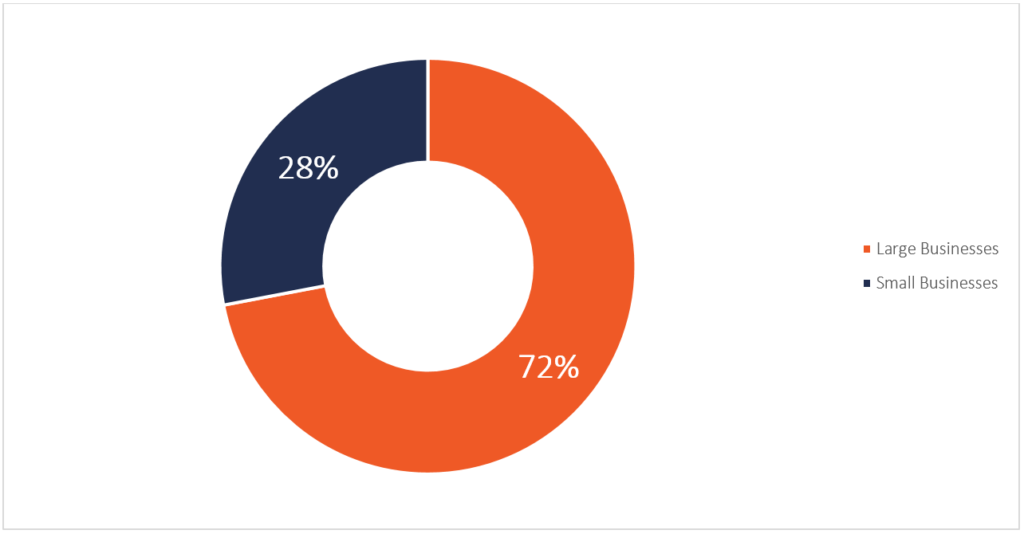
Of the breaches studied, 72% of breaches involved large businesses while 28% involved small businesses. This doesn’t mean that small businesses are off the hook, however, since these statistics are indicative of the companies surveyed and not necessarily the business community as a whole. Your small business still needs to take these basic measures (at the very least) to protect your clients and their data.
Varieties
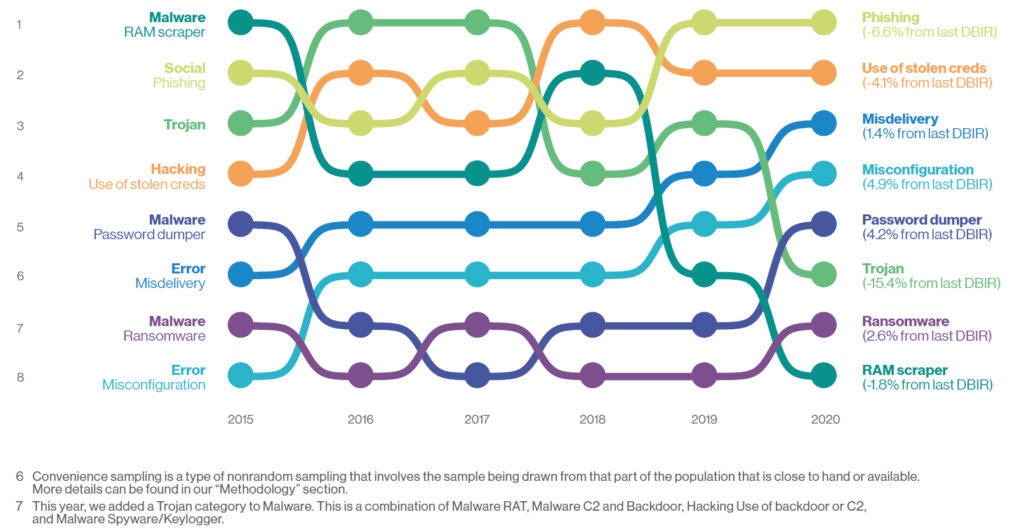
Over the last 5 years, the rate of incidence for common breach varieties has ebbed and flowed. This year, misdelivery, misconfiguration, password dumpers, and ransomware causes are all up.
Errors such as misconfigurations, misdeliveries, or publishing errors are as common as social breaches (i.e. phishing) and more common than malware breaches.
The top threat action varieties in this report for security incidents were DoS (hacking), phishing (social), and loss (error). For data breaches, the top causes were phishing (social) and use of stolen credentials (hacking).
Industry Findings
Overview
In this year’s report, the top industries surveyed with the most security incidents were:
- Professional, Scientific, & Technical Services
- Public Administration
- Information
- Finance & Insurance
- Manufacturing
- Education
- Healthcare
The top industries surveyed with the most data breaches were:
- Healthcare
- Finance & Insurance
- Manufacturing
- Information
- Public Administration
- Professional, Scientific, & Technical Services
- Education
Fast Facts
- 819 incidents and 228 data breaches with confirmed data disclosure
- 28% of breaches were phishing attacks
- 23% of breaches were hacking using stolen credentials
- External threat actors accounted for 67% of the breaches
- Internal threat actors accounted for 33% of the breaches
- The top actor motive was financial (92%)
- 1509 incidents and 448 data breaches with confirmed data disclosure
- Web application attacks and employee errors were among the top causes
- External threat actors accounted for 63% of the breaches
- Internal threat actors accounted for 35% of the breaches
- The top actor motive was financial (91%)
- 798 incidents and 521 data breaches with confirmed data disclosure
- Ransomware, lost/stolen assets, and human error were among the top causes
- External threat actors accounted for 51% of the breaches
- Internal threat actors accounted for 48% of the breaches
- The top motive was financial (88%)
- 5741 incidents and 360 data breaches with confirmed data disclosure
- Web app attacks via exploited vulnerabilities or stolen credentials and human error were among the top causes
- External threat actors accounted for 67% of the breaches
- Internal threat actors accounted for 34% of the breaches
- The top motive was financial (88%)
- 922 incidents and 381 data breaches with confirmed data disclosure
- Hacking attempts with password dumper malware and stolen credentials were among the top causes
- External threat actors accounted for 75% of the breaches
- Internal threat actors accounted for 25% of the breaches
- The top motive was financial (73%) but espionage was a close second at 27%
- 7463 incidents and 326 data breaches with confirmed data disclosure
- Hacking using stolen credentials, social engineering (i.e. phishing), and denial of service attacks were among the top causes
- External threat actors accounted for 75% of the breaches
- Internal threat actors accounted for 22% of the breaches
- The top motive was financial (93%)
- 6843 incidents and 346 data breaches with confirmed data disclosure
- Ransomware and misdelivery or misconfiguration were among the top causes
- External threat actors accounted for 59% of the breaches
- Internal threat actors accounted for 43% of the breaches
- The top motive was financial (75%)
Highlights & Key Takeaways
37% of all breaches stole or used credentials.
Of these, over 80% of hacking-type breaches involve brute force or the use of lost/stolen credentials. This underscores the importance of your company practicing good password hygiene organization-wide. Be sure to make your passwords long and strong with various characters (uppercase, lowercase, numbers, symbols, etc.). Don’t reuse passwords; if a hacker gets one of your passwords and you use it for all your accounts, you’re in big trouble. You should also use multi-factor authentication when it’s available. Learn more about these tips in our blog post, How Do Passwords Get Hacked?
22% of all breaches involved phishing.
Phishing is categorized as a social-type breach. Ninety-six percent of these action types were delivered via email, 3% via website, and via phone or text message around 1% of the time. The top goal for phishing breaches is to gain access to credentials through the use of deception. Employee security training is key to avoiding phishing success. Make sure your employees know the signs of a phishing attempt such as spelling mistakes, vague language, suspicious links, unexpected attachments, and mismatched sender names/email addresses.
Over 60% of breaches were discovered in days or less.
The faster a breach is discovered, the less havoc it can wreak. Verizon attributes this year’s fast response time to Managed Security Service Providers (MSSPs), like us, helping organizations quickly discover security incidents and data breaches.
North America had the most incidents and breaches.
In this year’s DBIR, North America accounted for 69% of all incidents and 55% of all data breaches, predominantly in Canada, Bermuda, and the United States. Whether accidentally or intentionally, 31% of these breaches were carried out by internal threat actors. The numbers may be higher due to North America’s stringent reporting standards, however, the mindset that data breaches happen to “other businesses but not mine” is a dangerous one. Breaches are right in our backyard and it’s important to take them seriously. A few cyber security precautions can go a long when in preventing irreparable damage to your business reputation and livelihood.






