Our lives are intricately intertwined with technology. Whether it’s at a desk or in the field, most of us are daily technology users. We use mobile apps to order food or catch a ride. Realize you forgot to lock your car but you’re already seven blocks away? Yep, there’s even an app for that. And those are just the more basic day to day uses of technology (did you know earbuds that translate other languages in near real-time are currently in the works?).
So it comes as no surprise that the technology industry is one of the fastest growing industries. In fact, it’s expected to reach $5 trillion this year, with the United States representing 31% of the total. It’s projected to keep growing, too. Conventionally, the tech industry is subdivided into five categories: hardware/software/services, telecom services, devices/infrastructure, IT/business services, and emerging technologies.
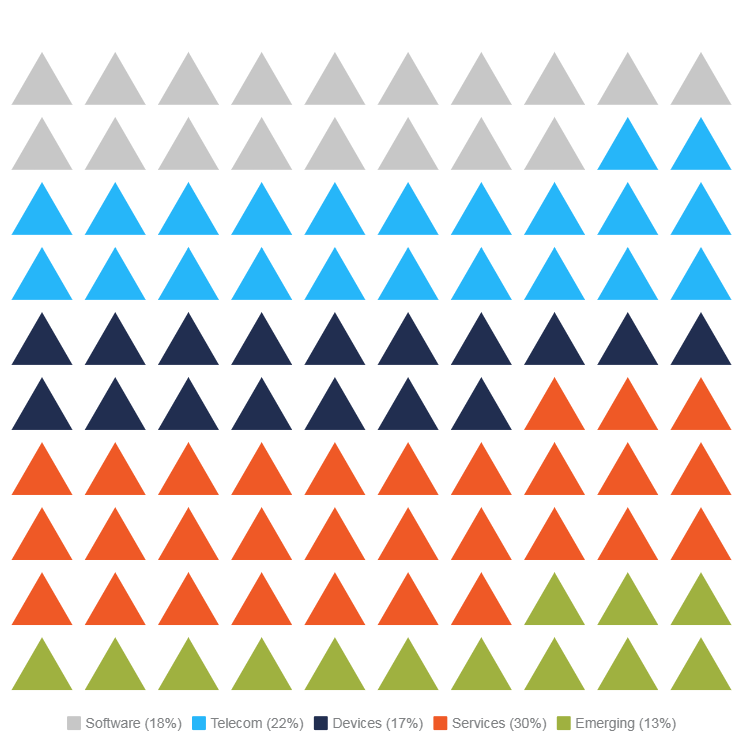
US Market [Source: IDC}
The Buzzwords
Agent
A small program that is installed on a PC that allows managed services providers to remotely monitor, manage, and resolve issues.
Asset Tracking
A way to keep track of your company’s inventory (i.e. employee computers). This also helps identify when upgrades need to be made.
Backup and Disaster Recovery (BDR)
A combination of solutions that helps ensure business continuity. You can think of BDR as assurance that you won’t lose everything when disaster strikes.
Block Hours
A service model where a customer buys a block of hours, generally at a discounted rate. Any work that is done to help the customer is then deducted from the pre-paid block of hours, instead of charged after the fact.
Cloud
According to Microsoft, “cloud computing is the delivery of computing services—servers, storage, databases, networking, software, analytics, intelligence and more—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale”.
Employee Security Training
This term differs depending on who you ask, but ADKtechs’ employee security training educates your team on how to defend your business against cyber criminals and prevent data breaches.
Encryption
The process of encoding information so that only authorized parties can access it and is a simple way to protect your data. Even though encryption doesn’t prevent interception, it does make your information inaccessible and intelligible if it happens to be stolen.
End of Life (EOL)
Indicates the end of a product’s useful life and end of manufacturer sale or support. An example is Windows 7, which reaches its end of life at the beginning of next year.
Endpoint Protection
Endpoints are devices connected to your network, such as desktops, laptops, tablets, and smart phones. Endpoint protection is a method of securing your network/devices and can encompass various methods of security such as anti-virus software, web content filtering, and patch management.
Ethical Hacker
Also known as a “white hat hacker”, an ethical hacker works to expose a system or network’s vulnerabilities in order to better secure it. We’re proud to have a number of Certified Ethical Hackers on our team.
Hardware as a Service (HaaS)
Similar to leasing, the HaaS procurement model allows a client to pay a fee to use hardware (such as a computer or server) that is owned and managed by a managed services provider.
Help Desk
A resource that provides a customer with support and answers to their questions.
Infrastructure as a Service (IaaS)
As the most basic type of cloud services, IaaS is when you rent IT infrastructure (services, storage, virtual machines, etc.) and pay-as-you-go.
In-House
When an organization hires its own IT staff. This is typically an expensive endeavor, as the organization not only has to oversee this team member but also has to pay for salary, benefits, and training.
Internet of Things (IoT)
According to Forbes, the Internet of Things “is the concept of basically connecting any device with an on and off switch to the Internet (and/or to each other). This includes everything from cellphones, coffee makers, washing machines, headphones, lamps, wearable devices and almost anything else you can think of”.
Managed Network Services
When you sign up for managed network services, your IT provider can view your network through a single pane of glass and see if there are any changes occurring within the network that may pose a threat or cause for concern.
Managed Security Services Provider
MSSPs assume ongoing responsibility for monitoring, managing, and/or problem resolution for selected IT systems on your behalf. They also offer services such as alerts, security monitoring, patch management, and on-site/off-site backup & recovery.
Managed Services Provider
MSPs proactively monitor and maintain your business technology. The managed services platform allows for you to have a more predictable IT budget on a year to year basis.
Mobile Device Management (MDM)
A type of security software used to track, monitor, and secure employee devices. This is especially important for companies that supply work-related PCs, cellphones, or tablets and need proper management of these devices when they reconnect to the company’s main network.
Network Assessment
Identifies the areas of your business that may put you at risk for a breach and cause downtime or frustrations. Our complimentary network assessment ensures that your servers, firewalls, routers, switches, etc. are properly configured; verifies that all critical security updates are deployed; reviews infrastructure and server environment for performance, storage, or configurations issues; and creates a plan of remediation.
Next Generation Firewall
Combines traditional firewall functionality with additional features such as threat intelligence and intrusion prevention to provide high-performing end to end protection.
Platform as a Service (PaaS)
A cloud service that provides an environment for development and testing applications.
Remote Monitoring & Management (RMM)
A platform of tools that monitors, manages, and deploys solutions to endpoints through the use of an agent installed on endpoint devices.
Service-Level Agreement (SLA)
A commitment between a service provider and client that details what the client will receive in respect to response times, quality of services, availability, etc.
Small and Medium-Sized Business (SMB)
Generally defined by number of employees (small: <100; medium: 100-999) or annual revenue (small: <$50M; medium: $50M-$1B). SMBs typically have smaller IT budgets, making them a prime target for malicious hackers.
Smart City
A municipality that combines information technology and communication technology to enhance municipal services in order to increase the quality of living for its residents. Examples include real-time commuter bus location updates or interactive 311 request maps.
Spam Filtering
An application that detects unwanted or dangerous emails before they hit your inbox, saving email users from potential phishing scams or other threats.
Software as a Service (SaaS)
Microsoft states that SaaS is “a method for delivering software applications over the Internet, on demand and typically on a subscription basis. With SaaS, cloud providers host and manage the software application and underlying infrastructure, and handle any maintenance, like software upgrades and security patching”.
Value-Added Reseller (VAR)
A business that resells a product after providing additional features or services. As a VAR, when you buy a PC from ADKtechs, we configure it and make sure it’s ready to get to work before it gets put on your desk.
Web Content Filtering
Helps decide which content is acceptable for viewing and access by checking the content against a set of rules. Web content filtering ensures that employees aren’t wasting time or putting a company at risk by accessing unsafe websites or downloading suspicious content.
Voice-Over Internet Protocol (VoIP)
To make and receive calls, VoIP technology utilizes the same data network you use for email and internet browsing.
The more you know...
Still have questions? We’d love to hear them!






